How to identify and prevent Apple phishing emails

Phishing emails targeting Apple users are becoming increasingly sophisticated, often imitating official communications from Apple to steal personal details or distribute malicious links. Recognizing these threats is the first step toward protecting your Apple Account (previously Apple ID), financial information, and digital privacy.
In this guide, we outline common red flags in suspicious emails, how to report them, and practical habits to reduce your exposure to them. With real-world examples and actionable advice, we provide the tools needed to protect your data and strengthen your online security.
What are Apple phishing emails?
Apple phishing emails are fraudulent messages designed to trick you into sharing sensitive information, such as your Apple Account credentials or payment details. These messages often imitate official Apple communications, using familiar logos, formatting, and sender addresses. Most create a sense of urgency, warning you that your account will be locked if you don’t take immediate action.
Apple Account credentials are especially valuable to cybercriminals because they provide access to services like iCloud, Apple Pay, the App Store, and even personal files and photos. A single compromised account can lead to financial losses, identity theft, or the sale of your information on the dark web.
Common types of Apple phishing scams
Phishing scams targeting Apple users can take many forms. Some scams impersonate Apple Support, alerting you to fake security issues in an attempt to harvest your credentials. Others may include fake invoices, gift cards, or urgent limited-time offers.
Storage limit alert scam
This scam claims that your iCloud storage is full and urges you to upgrade to avoid losing files. The email may include Apple’s branding and a button or link leading to a fake login page. If you enter your credentials, attackers can capture this information and may be able to use it to take over your account.
If you receive an email like this, check your iCloud storage directly in your device settings and upgrade only through your official Apple account, not through the email.
Fake purchase scam
A fake iTunes email may claim that an app, subscription, or product was purchased without authorization. To dispute the charge, the message directs you to a "support" link that requests your login details or payment information.
These scams exploit panic, prompting quick reactions without careful thought. A legitimate Apple invoice will always appear in the purchase history of your Apple ID account.
Password reset scam
A password reset scam starts with a message, often by email, text, or device alert, claiming that someone has requested a password reset for your Apple Account (or Apple ID). It urges you to click a link if you didn’t make the request.
A legitimate password reset notification from Apple appears only when you or someone with access to your account initiates it. If you receive one unexpectedly, treat it as suspicious. Apple will never ask for your password, verification codes, or other security details through unsolicited emails, texts, or phone calls.
In one variation, attackers may repeatedly trigger “Allow” and “Don’t Allow” prompts on your trusted device. If you tap Allow, you may receive a one-time verification code. Sharing that code gives the attacker everything they need to reset your password, change recovery settings, and lock you out of your account.
Apple Pay suspended scam
These emails claim that an Apple Pay account has been suspended due to suspicious activity. Victims are pressured to "reactivate" their accounts by providing sensitive information, including Apple Account credentials, payment card numbers, or by answering security questions.
Unlike official Apple messages, phishing versions often rely on threatening language and urgent deadlines. If Apple Pay security is ever a concern, it’s safer to check the Wallet app directly or contact Apple Support instead of responding to the email.
Apple gift card scam
Scammers may send emails claiming you’ve received an Apple gift card and need to click a link to redeem it. The link leads to a fake website that steals your credentials or payment details. Some versions ask you to verify personal information, while others demand a small payment before releasing the supposed reward. Some scam messages may include malicious attachments disguised as gift cards.
Apple never sends gift cards as file attachments, asks for sensitive information to redeem them, or requests money to unlock them, so treat any unexpected gift card emails with caution.
Fake support phone calls
While not strictly an email scam, phishing attempts often include messages instructing you to call a support number for help. Once connected, fake representatives may request remote access to your device or ask for payment details or gift card codes. If an email pushes you toward calling a number, always verify it through Apple’s official support page before engaging.
How to recognize a fake Apple email
Fake Apple emails often look convincing because they use Apple’s logos, colors, and style. To spot a fake Apple email, pay close attention to the sender's address, the wording used, and any included links or attachments.
Warning signs of phishing emails
Apple will never ask you to share personal information such as your full credit card number, Social Security number, or security codes through email. Requests for sensitive details, especially passwords or payment verification, are major red flags and reliable indicators of a phishing attempt.
Here are some other warning signs to look out for:
Formatting inconsistencies
Inconsistent fonts, low-quality images, and off-brand colors are often indicators of a scam, as official emails from Apple don’t contain these discrepancies.
You should also watch out for unusual spacing between letters (kerning). Cybercriminals may use letters or symbols that visually mimic legitimate text to bypass spam filters or deceive readers.
Poor grammar and spelling
Emails with typos, awkward phrasing, or unnatural sentence structure are strong indicators of a phishing attempt. Scammers often operate across borders, and rushed translations frequently give them away.
Even small grammatical mistakes, like wrong tenses or oddly placed punctuation, can indicate the message isn’t from Apple. If you notice repeated errors, consider the email to be highly suspicious, especially when it includes time-sensitive requests.
Generic greetings
Official Apple emails will use your full name or your Apple Account name. Phishing attempts, however, often begin with vague openings such as “Dear customer” or “Dear user.” This generic approach allows scammers to send the same email to thousands of people without customization.
Combined with other red flags, it’s a strong indicator the message isn’t authentic. A real Apple message will never address you generically when tied to account-specific issues.
Suspicious links and attachments
Links and attachments are often the most dangerous parts of phishing emails. Fake links may appear to lead to Apple websites but can redirect you to pages designed to steal your credentials. Be especially cautious of links from URL shortening services, which can hide a link’s real destination. Attachments are equally risky, as they may contain malware or prompt you to install harmful software.
To stay safe, avoid clicking on any links or attachments in messages that seem suspicious. Instead, sign in to your Apple account directly through Apple’s official website. If there is a legitimate issue with your account, it will appear there.
How to spot real vs. fake Apple communications
Apple’s official emails follow clear patterns. Genuine communications are polished, free of errors, and tied directly to your Apple Account. They never include threats, urgency, or random attachments. Fake emails, on the other hand, pressure you into acting quickly or providing sensitive details.
Verify the sender’s email address
One of the simplest ways to catch a phishing attempt is by checking the sender’s address. Official Apple messages come from “@apple.com” or a closely related domain. Fraudulent emails often use lookalikes, like “@app1e-support.com” or “@appl3.com,” hoping you won’t notice.
On desktop, hover over the sender name to reveal the full address; on mobile, tap to expand details. If the domain doesn’t exactly match Apple’s, treat the email as unsafe.
Some email providers, including Gmail and Apple Mail, also support Brand Indicators for Message Identification (BIMI), which allows organizations to display a verified company logo next to their authenticated emails. As a result, real emails from Apple will display the Apple logo as the sender avatar. In Gmail, you’ll also see a blue checkmark next to the sender name, which you can tap on to view the details of the verification.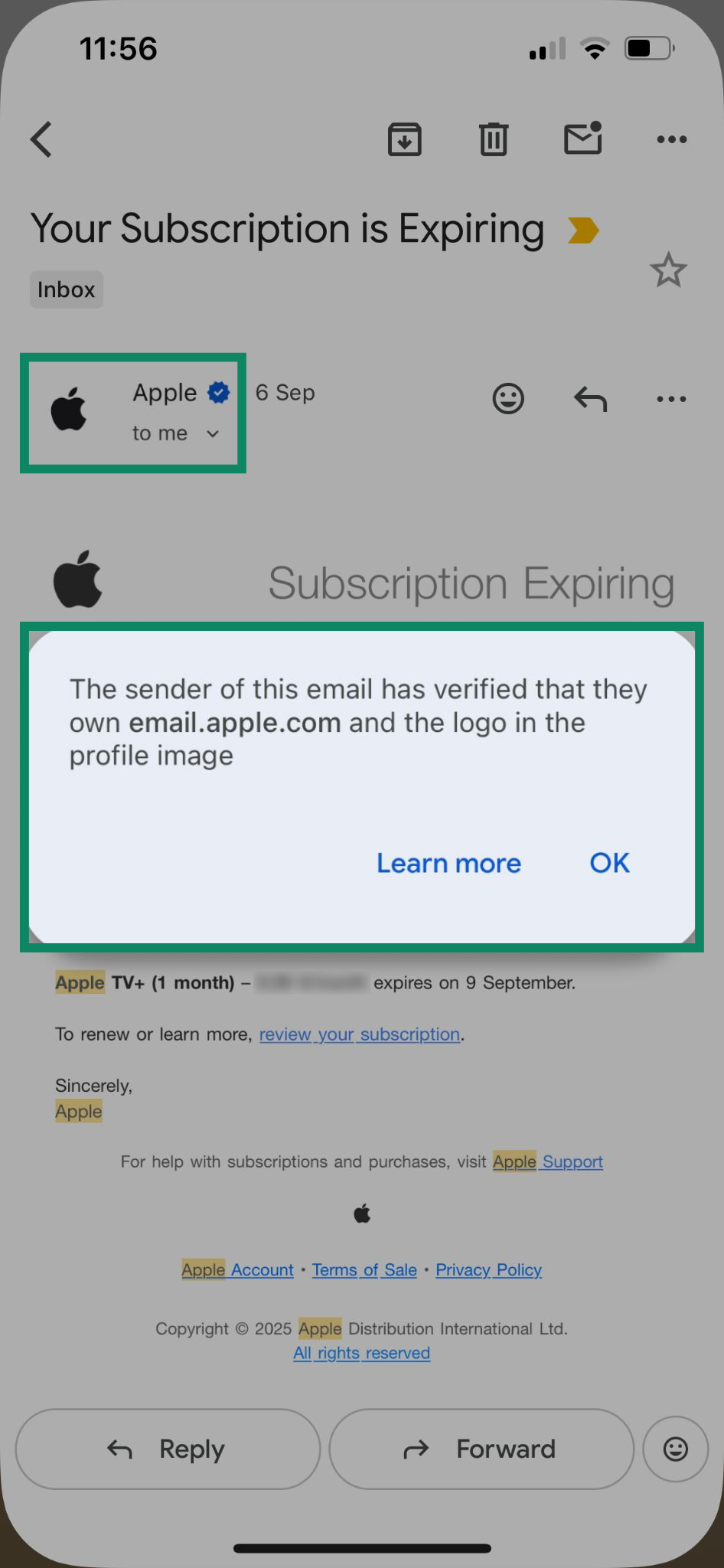
Signs of legitimate Apple emails
Legitimate Apple emails typically address you by name and use the language you’ve set in your Apple Account. This personalization helps distinguish real messages from generic phishing attempts.
All links in official Apple emails direct you to Apple domains, such as apple.com or icloud.com. To stay safe, hover over links on desktop or tap-and-hold on mobile to verify the URL before clicking.
Invoices and receipts in genuine emails will always match your purchase history in your Apple Account or iTunes. If a message claims a purchase you don’t recognize, it’s likely fraudulent.
How to report Apple phishing emails
If you receive a suspicious email, don’t click any links or download attachments. Instead, forward the message to Apple’s official reporting address. Make sure to include the email header details, as this helps Apple investigate the source. Reporting not only protects you but also assists in shutting down fraudulent operations. If you’re ever uncertain about a message, it’s safer to report it than to ignore it.
To help train your mail provider's spam filter to stop phishing emails in the future, mark the email as junk after forwarding it.
What to do if you clicked a phishing email
You can take steps to limit damage even after interacting with a phishing email. Acting quickly is critical to protecting your account and personal data.
Don’t enter personal information
If a phishing link directs you to a spoofed website, avoid entering sensitive data, such as passwords, credit card numbers, or Social Security numbers. Providing this information can lead to identity theft, financial fraud, or unauthorized account access. Instead, close the page and exit the browser immediately.
Change your Apple Account password immediately
If you entered your login credentials, reset your password from a trusted Apple device. If you don’t have one, you can use a device at an Apple Store or the Apple Support app on a friend or family member’s device. Use a strong, unique password and update your security questions.
How to change your Apple Account password on iOS
- Open the Settings app.
- Tap your Apple Account name at the top of the screen.
- Tap Sign-In & Security.
- Below Security, tap Change Password.
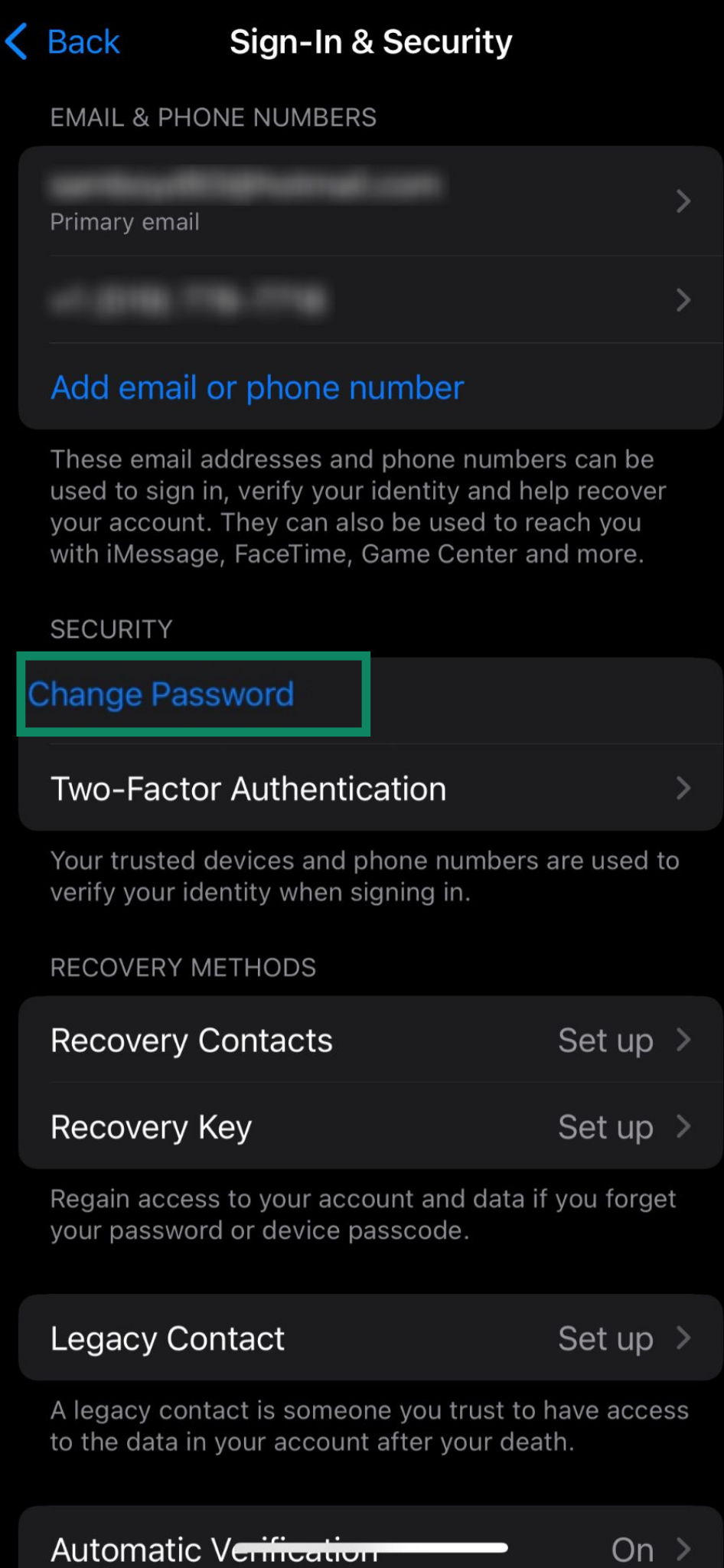
- Follow the on-screen instructions to update your password. You may be asked to verify your identity with Face ID, Touch ID, or another form of two-factor authentication (2FA) before continuing.
How to change your Apple Account password on macOS
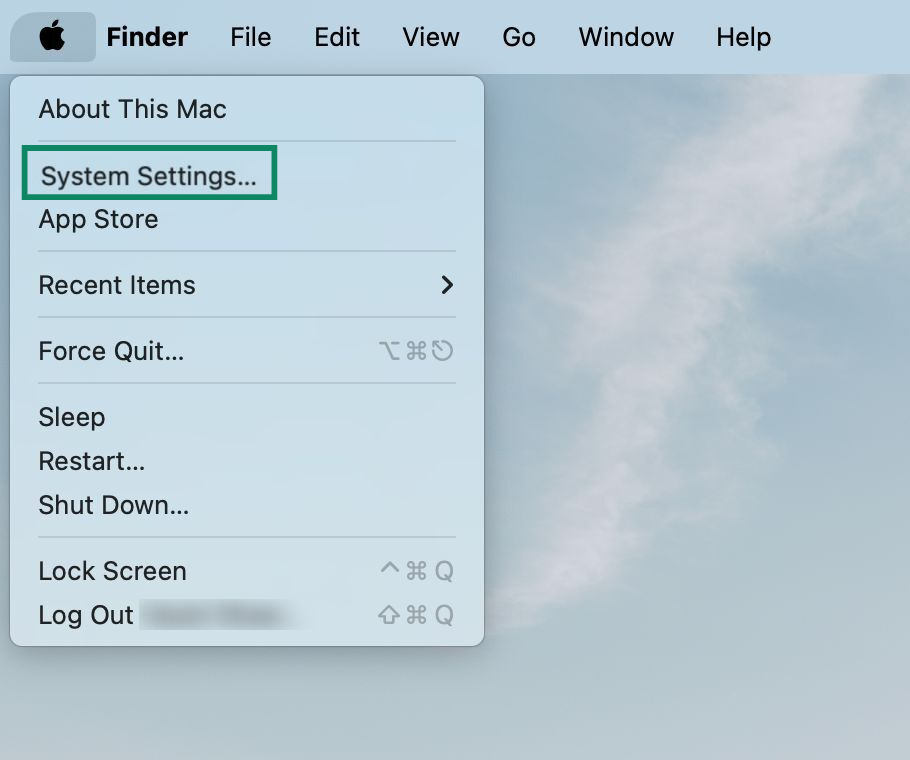
- Open the Apple Menu in the top-left corner of your screen.
- Select System Settings.
- Click Sign-In & Security.
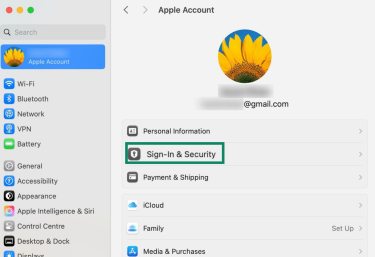
- Click Change Password.
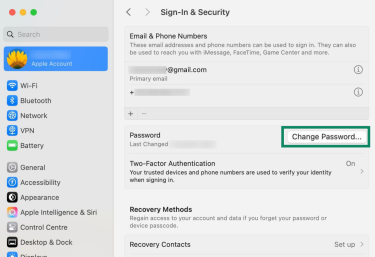
- Follow the on-screen instructions to update and confirm your new password.
Immediately stop any downloads and check your device
If you clicked a suspicious Apple email or attachment, pause any active downloads right away to prevent malware from reaching your device. Open your browser’s download list and remove any files that may have started downloading. You can also manually check for suspicious apps in the Applications folder, remove anything you don’t recognize, and clear your Safari history and website data to eliminate any cached malicious content.
Secure financial information
If you shared any payment details, such as credit card numbers, bank account information, or Apple Pay credentials, contact your bank or card provider immediately. Explain that the information may have been exposed in a phishing attack.
Monitor your accounts closely for any suspicious activity, and consider setting up fraud alerts if your bank offers them. Acting quickly can prevent financial loss and limit the damage from the compromise.
Report the fraud to the appropriate authorities
If you suspect you’ve been scammed or someone has attempted to steal your identity, notify local law enforcement and report the incident to the relevant authorities for your location. In the U.S., you can contact the Internet Crime Complaint Center (IC3).
Monitor accounts and devices
Review your Apple Account for unusual activity. Sign out of suspicious sessions, cancel unwanted subscriptions, and report any unauthorized charges to Apple.
- Visit account.apple.com and sign in.

- Click Devices and look for any devices you don’t recognize.
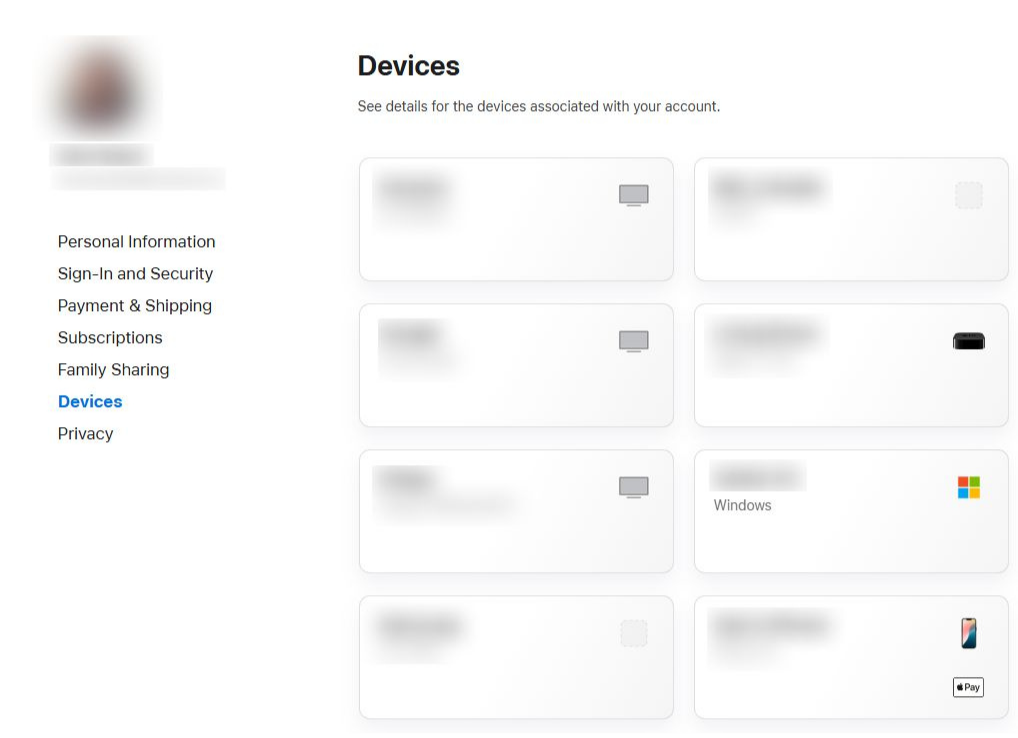
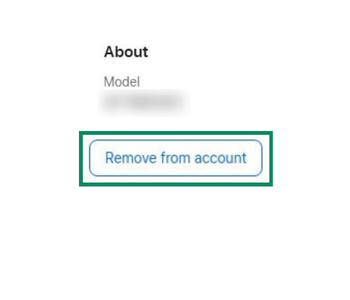
- If you see an unfamiliar device, select it and click Remove from account.
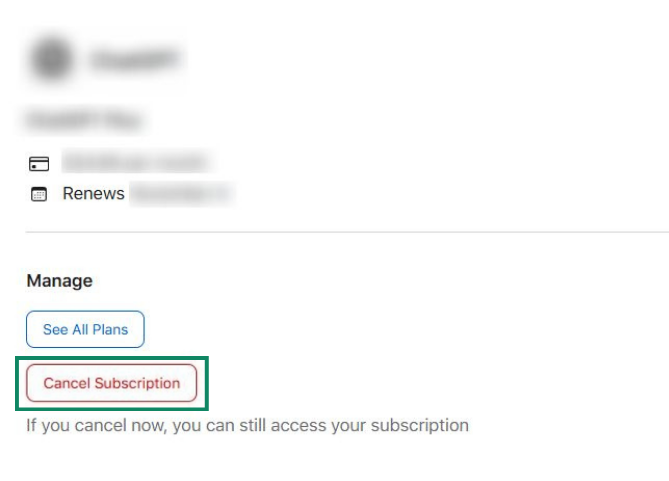
- Next, select Subscriptions. Click on any subscriptions you don’t recognize and choose Cancel Subscription.
- If you found any purchases you didn’t personally authorize, you can make a claim via reportaproblem.apple.com.
How to protect yourself from future Apple phishing attempts
Preventing phishing attacks requires strong digital habits and awareness of social engineering tactics. Scammers constantly adapt, so staying proactive is essential. Protecting an Apple ID begins with securing your account settings but also relies on awareness of evolving scam tactics.
Set a strong password
A strong, unique password forms the first line of defense. For example, a password like “Giraffe!92$TreeMoon” is much harder to crack than a simple one like “Apple123.” Reusing credentials across accounts also increases the risk of widespread compromise if one password leaks. Tools like ExpressKeys help by generating and storing complex logins securely, removing the need to memorize them.
Protect your email
Equally important is protecting the email address linked to your Apple Account, since attackers often target emails first. On iPhone and iPad, the Mail app includes a feature called Protect Mail Activity. It hides your IP address and prevents senders from seeing when you open emails, stopping them from tracking interactions or targeting you with phishing. You can enable this feature and adjust any other preferences for the Mail app in your iPhone settings.
Use multi-factor authentication
Multi-factor authentication (MFA) is one of the most effective defenses for an Apple Account. It requires both a password and a verification code sent to a trusted device. Even if credentials are stolen, attackers can’t log in without the second factor. MFA can be enabled directly from your Apple Account settings, and leaving it disabled leaves accounts significantly more vulnerable.
Stay informed about new Apple scams
Scammers constantly refine their tactics, meaning yesterday’s red flags may not look the same tomorrow. Staying updated helps identify new phishing methods before they cause problems. Keep an eye on trusted tech news outlets or cybersecurity blogs to stay aware of emerging scams and security alerts.
Use ExpressVPN’s Threat Manager
ExpressVPN’s Threat Manager can add an extra layer of protection by preventing your device from communicating with servers listed on our blocklist of known trackers and malicious sites. While it can’t stop every online threat, it helps reduce the risk of visiting fake login pages or interacting with other harmful content.
FAQ: Common questions about Apple phishing emails
How do I know if an Apple email is legit?
You can recognize legitimate Apple emails by checking the sender address, looking for personalized greetings, and verifying links before clicking. Genuine messages will come from domains like @apple.com, address you by name, and never ask for sensitive information such as your password or full payment details.
Always cross-check claims by logging into your Apple account directly rather than following email links, and be cautious of urgent language or attachments that seem suspicious.
What are the most common Apple phishing scams right now?
Current Apple phishing scams often involve fake invoices, storage alerts, and password reset notices designed to trick you into providing credentials or payment info. Scammers also target Apple Pay, gift cards, and digital wallets with emails or messages that appear urgent or threatening. Understanding these common tactics can help you spot red flags, such as generic greetings, spelling errors, or mismatched sender domains, before any damage occurs.
How can I secure my Apple ID against phishing attempts?
Securing your Apple Account (formerly Apple ID) starts with using a strong password and multi-factor authentication to prevent unauthorized access. It’s also important to learn how to recognize phishing attempts and what to do if you accidentally engage with one, so you can act quickly to secure your account.
Are Apple Pay and gift cards targeted in phishing scams?
Sometimes, yes. Apple Pay and gift card scams can be used by cybercriminals to convert stolen information into immediate financial gain. Phishing emails may claim your Apple Pay account is suspended or that you’ve received a gift card that requires verification. These messages often ask for login credentials or payment details, which Apple never requests via email. Always confirm any claims through official Apple apps or websites rather than responding directly to the message.
Take the first step to protect yourself online. Try ExpressVPN risk-free.
Get ExpressVPN